SWIFT on Monday heavily rejected allegations by officials in Bangladesh that technicians with the global banking system made the nation’s central bank more vulnerable to hacking before an $81 million cyber heist in February.
The comments were in response to a Reuters story that cited Bangladeshi police and a central bank official as saying that SWIFT technicians introduced security holes into the bank’s network while connecting SWIFT to Bangladesh’s first real-time gross settlement (RTGS) system.
bank official as saying that SWIFT technicians introduced security holes into the bank’s network while connecting SWIFT to Bangladesh’s first real-time gross settlement (RTGS) system.
In a report on April 25, Reuters said: “Developments coming to light in the unprecedented cyber-heist suggest that a lynch pin of the global financial system [the Swift network] could be more vulnerable than previously understood because of weaknesses that enabled attackers to modify a Swift software programme installed on bank servers.”
In Reuters report: “Bangladesh’s central bank became more vulnerable to hackers when technicians from Swift, the global financial network, connected a new bank transaction system to Swift messaging three months before a $81m cyber heist, Bangladeshi police and a bank official alleged.” In the same report, Reuters admitted it was not able to independently verify the allegations by Bangladeshi officials about the Swift technicians and Swift itself declined to comment.
Frustrated by some of the press reports and the failure of Bangladesh central bank to provide more details of the heist, Swift has sent a strongly worded letter to its users explaining its position.
It begins: “Dear Swift user, We are writing in the wake of the recent incident, in light of the prolonged silence from the user concerned and the ongoing speculation regarding Swift. First and foremost, we wish to reassure you again that the Swift network and Swift messaging systems have not been compromised.”
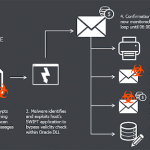
The letter continues later: “From what we know of the incident in question, the attackers had good knowledge of the bank’s systems and their security procedures. Using that knowledge they were able to compromise the bank’s environment, access its core banking systems, generate messages, gain the credentials to the bank’s Alliance Access system [Swift software] and thereby send the fraudulent messages. How complex the compromise was, versus how weak the user’s security environment was, remains unknown. It is still also unknown whether the compromise and fraud were led or facilitated by malicious insiders, or managed remotely.”
Swift confirms press reports that the attackers used a piece of malware that targeted Bangladesh Bank’s Alliance Access system to “disguise the traces of the fraudulent messages”. Swift responded by issuing an update to its software even though it was aware that this could be misconstrued by competitors as network vulnerability.
The letter to users says: “Contrary to the inevitable public commentary, the update is not a patch; it does not repair a vulnerability in the software or its interconnectivity with the messaging system and it cannot prevent a user’s environment being compromised… the update simply assists Alliance users to protect their local environment by helping them identify whether attackers have attempted to wipe their traces at the interface level after having already compromised their environment and injected fraudulent messages.”
Swift goes on to make the point that any system is only secure if it is held in a secure environment. “Swift is not, and cannot, be responsible for your decision to select, implement (and maintain) firewalls, nor the proper segregation of your internal networks; we cannot be responsible for selecting your staff and the distribution of credentials and allocation of permissions among them; nor for implementing your security access mechanisms and ensuring their proper maintenance, nor for designing your other security systems and procedures,” it says.